Mastering AES-256 Encryption and Decryption in C#
Securing Sensitive Data Made Simple
Data security is no longer optional — whether you’re protecting user credentials, API keys, or confidential configuration files.
In .NET and C#, one of the most reliable ways to protect data at rest or in transit is by using AES-256 encryption — a symmetric encryption standard trusted worldwide for its speed and strength.
In this guide, we’ll explore:
🔸 What AES-256 is and why it matters
🔸 How to implement AES-256 encryption and decryption in C#
🔸 Practical tips for using it securely in real-world apps
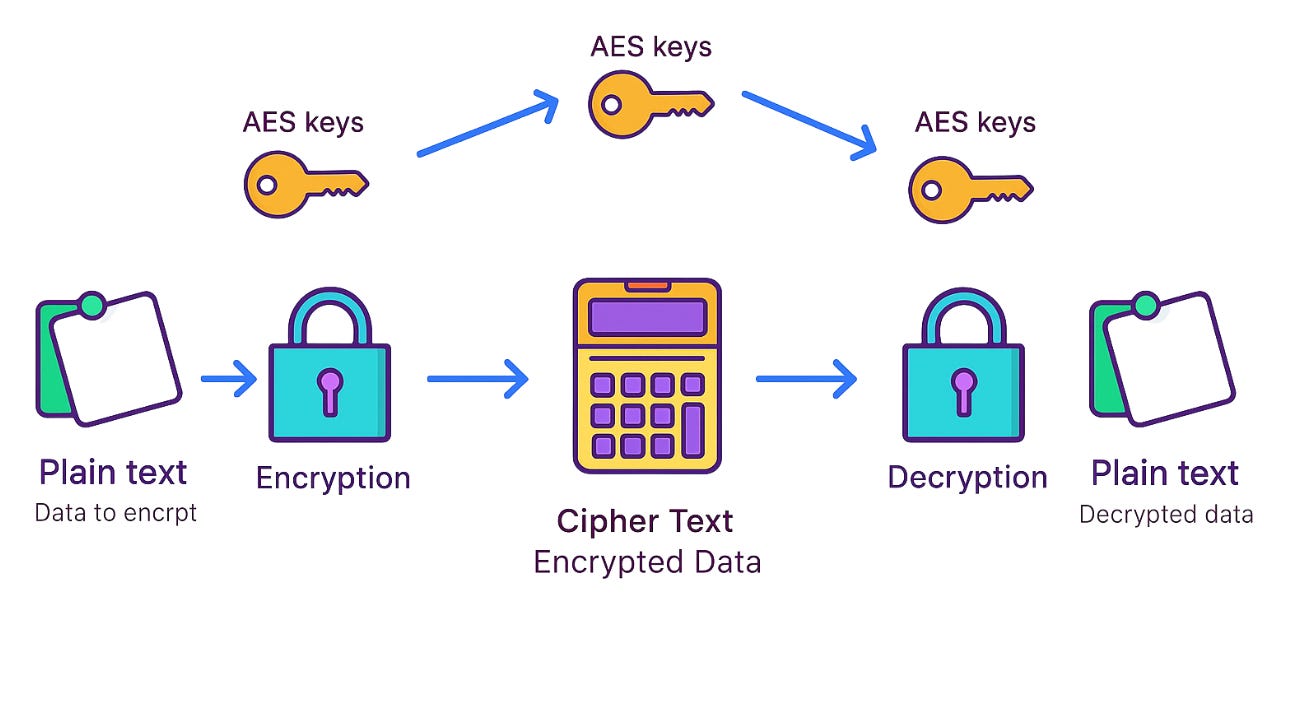
🧩 What is AES-256?
AES (Advanced Encryption Standard) is a symmetric encryption algorithm — meaning the same key is used to both encrypt and decrypt data.
The “256” in AES-256 refers to the key size — a 256-bit key provides 2²⁵⁶ possible combinations, making brute-force attacks virtually impossible.
It’s widely used in:
Secure messaging apps
Encrypted databases
File and password storage
Network communications (TLS, VPNs, etc.)
🧩 What is AES-256?
AES (Advanced Encryption Standard) is a symmetric encryption algorithm — meaning the same key is used to both encrypt and decrypt data.
The “256” in AES-256 refers to the key size — a 256-bit key provides 2²⁵⁶ possible combinations, making brute-force attacks virtually impossible.
It’s widely used in:
Secure messaging apps
Encrypted databases
File and password storage
Network communications (TLS, VPNs, etc.)
⚙️ Implementing AES-256 Encryption in C#
C# makes encryption straightforward through the System.Security.Cryptography namespace.
Let’s implement a helper class that can encrypt and decrypt strings using AES-256.
🔧 Full Code Example
using System;
using System.IO;
using System.Security.Cryptography;
using System.Text;
public static class AesEncryptionHelper
{
// Encrypt a plain text string using AES-256
public static string Encrypt(string plainText, string key)
{
using Aes aes = Aes.Create();
aes.Key = SHA256.HashData(Encoding.UTF8.GetBytes(key)); // Generate a 256-bit key
aes.GenerateIV(); // Create a random IV for each encryption
using var encryptor = aes.CreateEncryptor(aes.Key, aes.IV);
using var ms = new MemoryStream();
ms.Write(aes.IV, 0, aes.IV.Length); // Prepend IV to ciphertext
using (var cs = new CryptoStream(ms, encryptor, CryptoStreamMode.Write))
using (var writer = new StreamWriter(cs))
{
writer.Write(plainText);
}
return Convert.ToBase64String(ms.ToArray());
}
// Decrypt a cipher text string using AES-256
public static string Decrypt(string cipherText, string key)
{
byte[] fullCipher = Convert.FromBase64String(cipherText);
using Aes aes = Aes.Create();
aes.Key = SHA256.HashData(Encoding.UTF8.GetBytes(key));
// Extract IV from the beginning
byte[] iv = new byte[aes.BlockSize / 8];
Array.Copy(fullCipher, iv, iv.Length);
int cipherStartIndex = iv.Length;
int cipherLength = fullCipher.Length - cipherStartIndex;
using var decryptor = aes.CreateDecryptor(aes.Key, iv);
using var ms = new MemoryStream(fullCipher, cipherStartIndex, cipherLength);
using var cs = new CryptoStream(ms, decryptor, CryptoStreamMode.Read);
using var reader = new StreamReader(cs);
return reader.ReadToEnd();
}
}🧠 Example Usage
string secretKey = "MySuperSecretKey@123";
string plainText = "Hello AES 256 Encryption!";
string encrypted = AesEncryptionHelper.Encrypt(plainText, secretKey);
Console.WriteLine($"🔒 Encrypted: {encrypted}");
string decrypted = AesEncryptionHelper.Decrypt(encrypted, secretKey);
Console.WriteLine($"🔓 Decrypted: {decrypted}");🧩 How It Works
Key Derivation:
We useSHA256.HashData()to convert the input key into a 256-bit key required by AES-256.IV (Initialization Vector):
A random IV is generated each time to ensure the same plain text never produces the same cipher text.CryptoStream:
Handles the heavy lifting of encrypting and decrypting data streams securely.Base64 Encoding:
Converts binary data to text — making it easy to store or transmit over APIs, JSON, or databases.
🧱 Best Practices for AES-256 in .NET
✅ Use a strong, random key — don’t hard-code it in your source code.
✅ Always use a unique IV for every encryption (as shown above).
✅ Store key and IV securely (e.g., Azure Key Vault, AWS KMS, or environment variables).
✅ Prefer AES-GCM mode for modern applications if authenticated encryption (integrity + confidentiality) is needed.
✅ Avoid reusing encryption logic for passwords — use hashing algorithms like PBKDF2, bcrypt, or Argon2 instead.
🧾 When to Use AES-256
Use AES-256 when:
You need to store confidential configuration data (connection strings, API keys).
You must encrypt local files or backups.
You’re transmitting sensitive data between services without TLS.
🏁 Wrapping Up
AES-256 provides a powerful, efficient, and secure way to encrypt data in C#.
With just a few lines of code, you can protect your application from data leaks and unauthorized access.
💬 How are you currently handling encryption in your .NET applications?
Have you tried implementing AES-256 or another cipher?
👉 Full working code available at:
🔗https://sourcecode.kanaiyakatarmal.com/AesEncryptionSample
I hope you found this guide helpful and informative.
Thanks for reading!
If you enjoyed this article, feel free to share it and follow me for more practical, developer-friendly content like this.