5-way Multi Tenant Identification Strategy
A Quick Guide to Understanding Multi-Tenant Architecture in Software Design
𝗪𝗵𝗮𝘁 𝗶𝘀 𝗠𝘂𝗹𝘁𝗶-𝗧𝗲𝗻𝗮𝗻𝗰𝘆?
In today’s world of SaaS and cloud computing, the term multi-tenancy is more than just a buzzword—it's a core architectural pattern that powers scalable and cost-effective solutions.
So, what exactly is multi-tenancy?
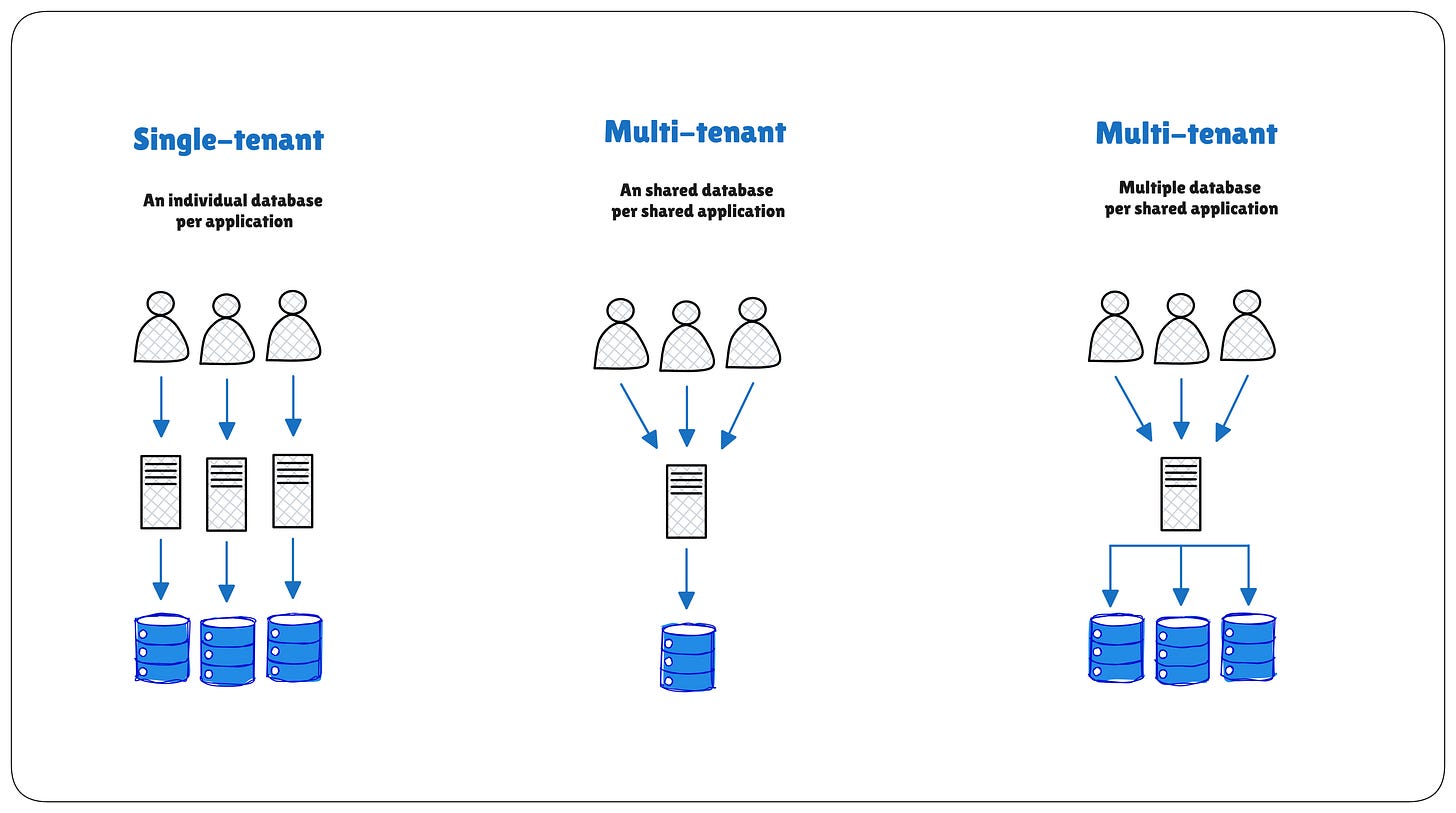
Multi-tenancy is a software architecture where a single instance of an application serves multiple customers, called tenants. Each tenant is isolated logically (not physically), meaning they use the same software and infrastructure but have their own data and configuration.
Think of it like an apartment building. Each tenant (customer) lives in a separate unit, but all units share the same building (application/server).
💡 In multi-tenant SaaS applications, securely and accurately identifying tenants is critical for data isolation, security, and personalized experiences. Whether you're building for startups or large enterprises, getting this layer right prevents cross-tenant access risks and ensures scalable architecture.
Here are 5 common strategies to identify tenants in a multi-tenant system:
1. Subdomain-Based Identification
Example: acme.yourapp.com
Each tenant gets a unique subdomain. The application parses the subdomain to determine the tenant.
✅ Pros:
Clear visual separation
Easy for customers to remember
Works well with DNS and SSL wildcard setup
⚠️ Cons:
Extra DNS configuration
Complex for local development and wildcard SSL handling
2. Path-Based Identification
Example: yourapp.com/tenants/acme
The tenant ID is included as part of the URL path.
✅ Pros:
Simple to implement
No DNS issues
⚠️ Cons:
Less elegant URLs
Slightly less secure if not validated strictly
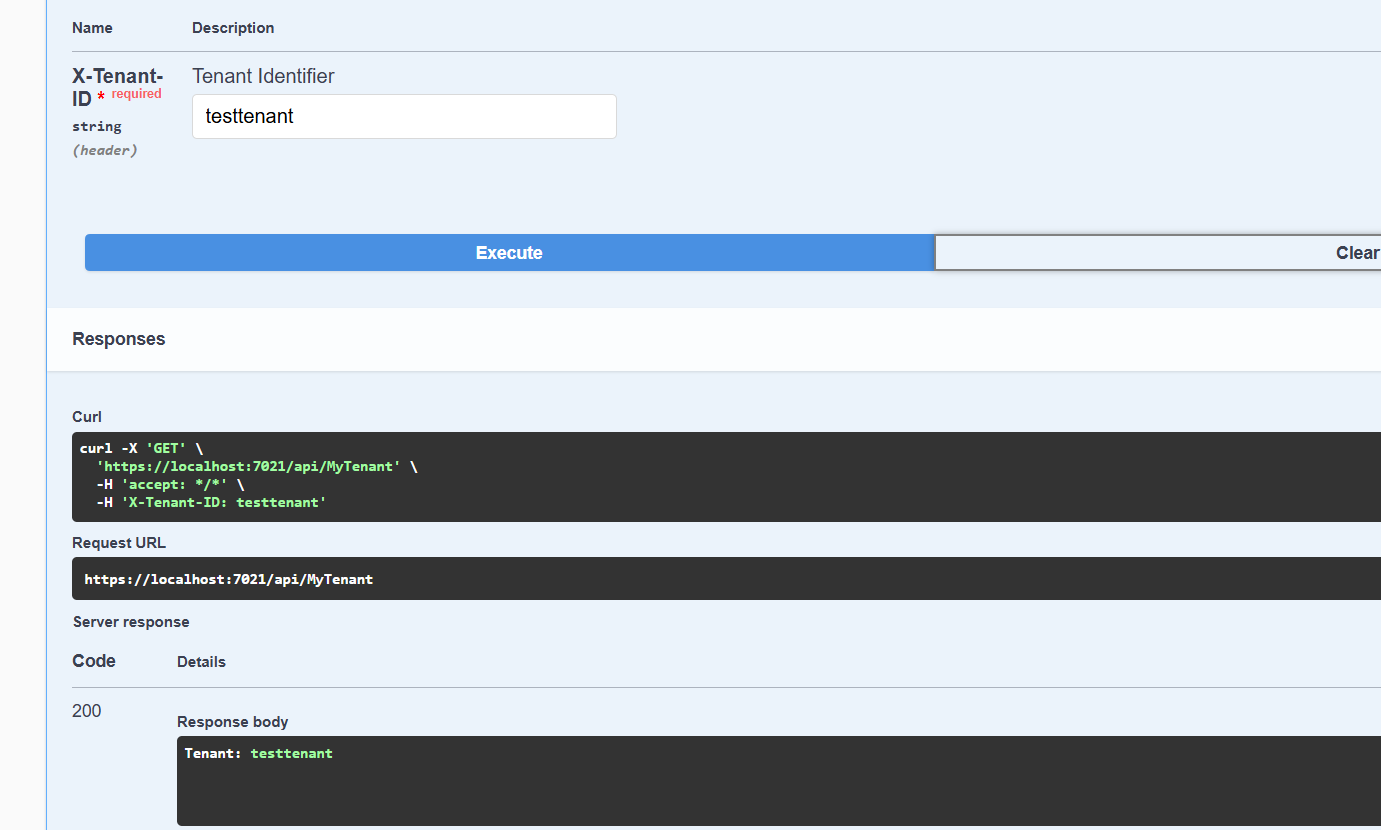
3. Header-Based Identification
Example: X-Tenant-ID: acme (sent in request headers)
Commonly used in internal APIs or secure microservice architectures.
✅ Pros:
Works great with API gateways
Clean URLs and decouples routing
⚠️ Cons:
Requires clients to set headers correctly
Not visible in logs unless captured explicitly
4. Token/Claims-Based Identification
Example: JWT -> { "tenant_id": "acme" }
Tenant information is embedded in an authentication token like JWT.
✅ Pros:
Secure and stateless
No URL/path pollution
Works great for mobile and backend APIs
⚠️ Cons:
Token must be validated on every request
Requires robust authentication layer
5. Query-Based Identification
Example: yourapp.com/api/orders?tenant_id=acme
The tenant ID is passed as a query string parameter in API calls.
✅ Pros:
Extremely simple to implement
Useful for API-based integrations or ad hoc access
⚠️ Cons:
Less secure if not validated properly
Easy to manipulate — requires strict access control and sanitization
Not ideal for public-facing URLs
Why Do We Need Multi-Tenancy?
Several factors drive the need for multi-tenancy:
Cost Efficiency: By sharing resources among multiple tenants, businesses can significantly reduce infrastructure and maintenance costs.
Scalability: Multi-tenant architectures can more easily accommodate growth in the user base without requiring proportional increases in resources.
Easier Maintenance: With only one application instance to manage, updates and maintenance become simpler and more streamlined.
Consistent Performance: Resource sharing allows for better utilization and more consistent performance across all tenants.
Rapid Deployment: New tenants can be onboarded quickly without the need to set up separate infrastructure.
Operational Efficiency: Centralized management reduces operational overhead and simplifies monitoring and support processes.
Data Insights: With data from multiple tenants in one place, it’s easier to derive valuable insights and improve the product.
Models of Multi-Tenancy
Multi-tenancy can be implemented at various levels of the application stack:
Application Level: A single instance of the application code serves multiple tenants, with customization handled through configuration.
Database Level: Tenants share a database system, but their data is segregated through different schemas or tables.
Infrastructure Level: Multiple tenants share the same physical or virtual infrastructure, with isolation provided by the platform.
Combination Approaches: Many real-world implementations use a combination of these models to balance security, performance, and resource efficiency.
Implementation
public class TenantInfo
{
public string TenantId { get; set; }
public string Name { get; set; }
// Add more as needed
} public interface ITenantProvider
{
TenantInfo CurrentTenant { get; }
void SetTenant(TenantInfo tenant);
}
public class TenantProvider : ITenantProvider
{
private TenantInfo _currentTenant;
public TenantInfo CurrentTenant => _currentTenant;
public void SetTenant(TenantInfo tenant) => _currentTenant = tenant;
}public class TenantResolutionMiddleware
{
private readonly RequestDelegate _next;
public TenantResolutionMiddleware(RequestDelegate next) => _next = next;
public async Task Invoke(HttpContext context, ITenantProvider tenantProvider)
{
string tenantId = context.Request.Headers["X-Tenant-ID"];
if (string.IsNullOrEmpty(tenantId))
{
tenantId = context.Request.Query["tenant"]; // fallback
}
if (!string.IsNullOrEmpty(tenantId))
{
// TODO: Validate tenant from DB or cache
tenantProvider.SetTenant(new TenantInfo { TenantId = tenantId });
}
await _next(context);
}
}📄 Result from Swagger UI
🛠 Pro Tip:
In real-world systems, hybrid strategies are common. For example, you may use subdomain-based routing for web portals, JWT claims for mobile apps, and headers or query params for third-party APIs.